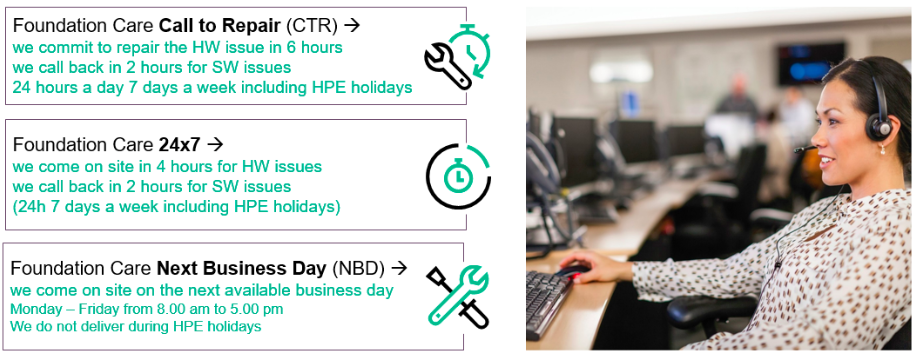
Start off right Work closely with our team of security experts before, during, and after your Proofpoint deployment. We provide: Review of your current deployment and help design policies and procedures for implementation Periodic solution health checks to make sure everything is working to plan People activate today’s integrated attacks. Email remains the #1 threat…
Category: News
Work stands out with exceptional color performance Special print mode for a wider color range and extra vividness for documents and marketing materials. Look professional with vibrant, high-quality color prints that can stand the test of time Get professional quality and performance with Original HP Toner cartridges and drums with JetIntelligence. Produce full-bleed A3 marketing…
Marvell PAM4 Optical DSP for AI and Cloud Interconnects a leader in data infrastructure semiconductor solutions, today announced Spica Gen2-T, the industry’s first 5nm 800 Gbps transmit-only PAM4 optical DSP. Designed for transmit retimed optical modules (TRO modules), Spica Gen2-T can reduce the power consumption of 800 Gbps optical modules by more than 40%1 while maintaining…
Warranties help us make secure purchases knwoing when things go wrong we have the support. When I’m out shopping, I may not buy every extended warranty for every home appliance, but I do like the peace of mind that comes with knowing that a manufacturer stands behind its product, especially for big-ticket items. https://www.youtube.com/watch?v=I5IR8Qq9-0k In…
Your Visibility with Control to Defeat Malware Across the Extended Network Hackers are creating advanced malware that can evade even the best point-in-time detection tools, like antivirus and intrusion prevention systems. This leaves IT security teams blind to the scope of a potential compromise and unable to quickly detect and remediate malware before it causes…
At V Get it We have realized that The global network security market is experiencing constant growth as a result of the growing virtualization of servers. While network threats have existed for decades, the time between vulnerability and exploit is shrinking. Organizations are being forced to spend more money on investigations, notifications and response when…